Recently, due to a renewed discussion in the OAuth Working Group, the recommended approach for securing browser-based applications (such as JavaScript SPAs) has changed.
Previously the recommendation was to use the implicit flow where access tokens where returned directly from the authorization endpoint via the URL. If you use OpenID Connect and IdentityServer4, then further steps are taken to secure this access token via the use of the hash fragment response mode and at_hash validation.
The new recommendation is to use the authorization code flow in combination with PKCE. This approach allows tokens to be completely removed from the URL, while still giving the authorization server/client a mechanism to ensure that authorization codes are not being injected in the application.
If you are using only OAuth 2.0, then it is recommended that you update your applications to use the authorization code flow and PKCE. If you are using OpenID Connect and IdentityServer4, then the urgency to upgrade is lessened but still recommended. In this case, the main benefit is that you are completely removing tokens from the URL securing you from risks such as misconfigured servers.
Migrating Existing Applications
If you are using oidc-client-js, thankfully the migration process is a simple case of updating your library and IdentityServer4 client configuration. Check out our article for full migration steps.
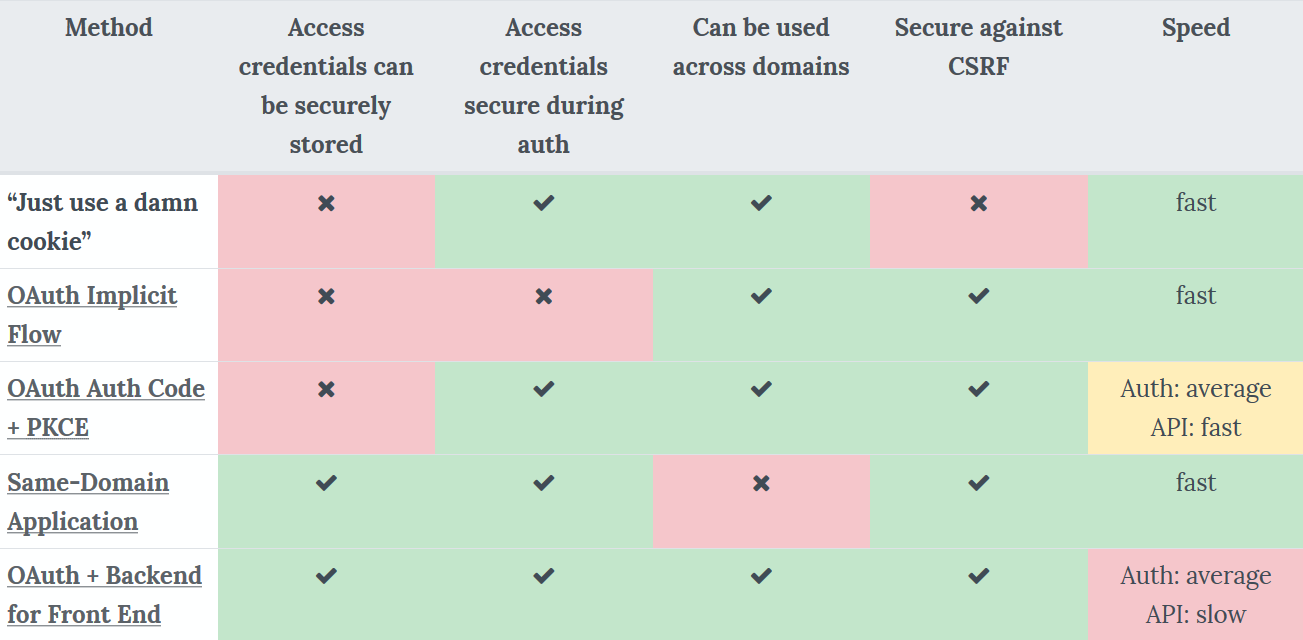
Creating New Browser-Based Applications Thanks to the renewed discussions about browser-based applications, some new approaches to securing them have been proposed, for example, the usage of same-site cookies, and backends for frontends. To help you choose the correct approach for your application, check out our OAuth cheat sheet.
Securing AdminUI
Our IdentityServer4 management tool, AdminUI, currently uses OpenID Connect and the implicit flow. In the upcoming update (2.4), we will be upgrading this to use the authorization code flow with PKCE. Our client application wizard will also be updated to allow for this new style, and also to enable PKCE across all other applicable application types.
What’s Next?
If you’re looking for expert advice on how to secure your browser-based applications with OAuth and OpenID Connect, then feel free to get in contact at sales@identityserver.com.

















